What are the developer's responsibilities due to the hack? Case study based on Impossible Finance hack.

On Jun-21-2021 04:39:07 AM +UTC, Impossible Finance got hacked for $500k using the same exploit as the one used on the BurgerSwap.
The issue was with the swap function supposed to verify if x*y>k, basically the requirement for Uniswap AMM to work correctly. Without this check, anyone can trigger a swap of the same price of the same tokens twice. It wouldn't be possible as there would be a slippage.
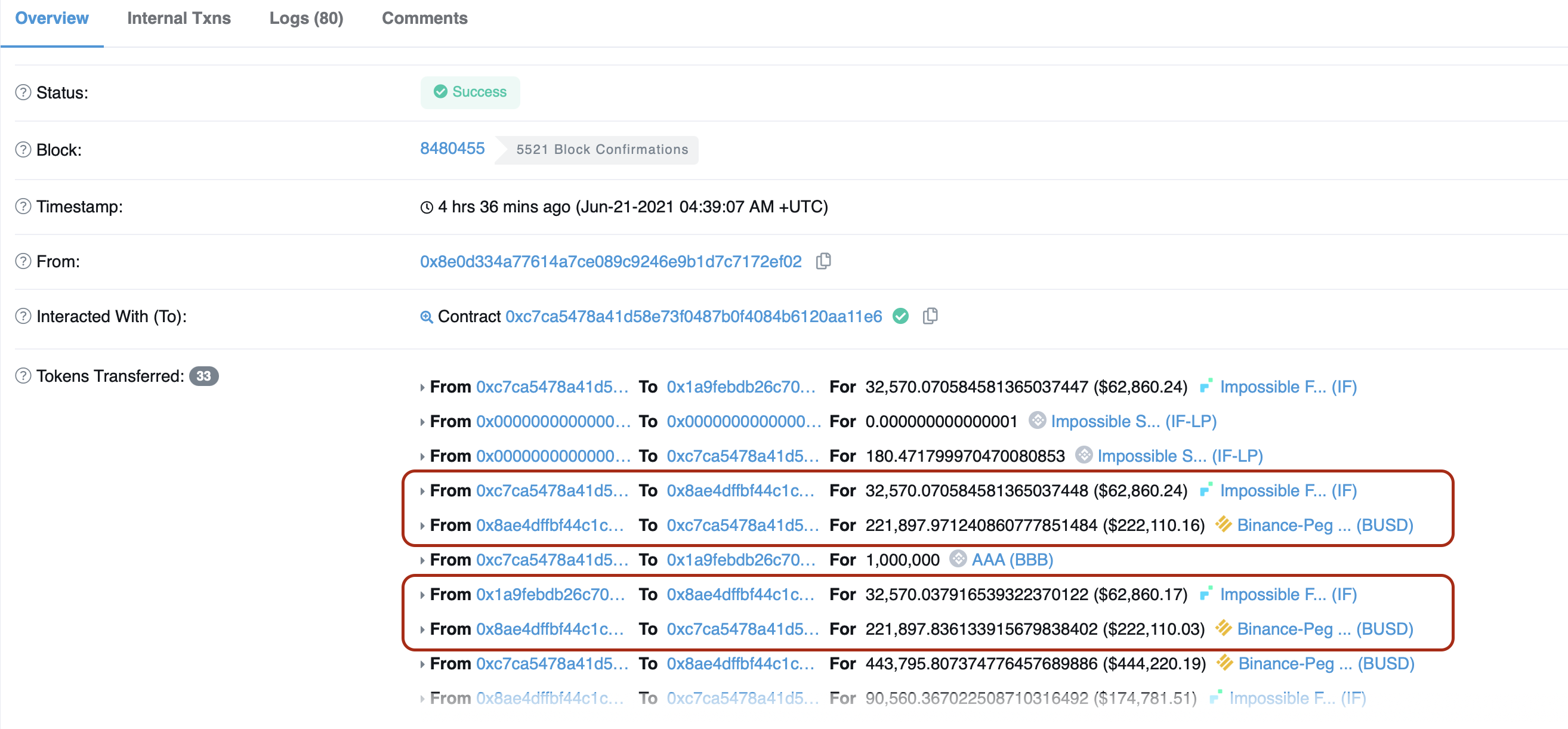
As a result, the hacker got away with $500k worth of Ether with Anyswap.
WatchPug did a highlight of the exploit.

What I want to focus on is the developer's responsibility. I said it many times. Audits are no silver bullets for your code quality and security. It's an extensive code review that is supposed to verify any assumptions and dismiss any security issues. But you, as a developer and creator of the projects, have the full responsibility of the overall quality of the code and if you follow best practices.
If you decide to fork from a project that has a known vulnerability or it was disclosed or hacked after you forked, you have an obligation to patch the code. You have the responsibility to follow closely if any exploits happened to the code you forked. You should be monitoring the situation closely. Even if you haven't forked the code but have the same design decision as to the hacked project (See BurgerSwap exploit), you must also fix your code, especially if you had to fix a vulnerability over a month.
Another thing is the removal of such crucial requirements in the code. It shows ignorance of the developers or lack of understanding of the forked code. I don't know which is worse.
Follow best practices, don't change code you don't understand, and audit your code before going public. Continuously monitor and stay up to date with the recent hacks, and analyze them. If you don't do that, you will be hacked.
Thanks for reading, and if you like my writing, you can subscribe to my blog to receive the daily newsletter as I'm currently in the middle of 100 days of blogging challenge. Subscription box below 👇
If the newsletter is not your thing, check out my Twitter @adrianhetman, where I post and share exciting news from the Blockchain world and security.
See you tomorrow!

